Eight Eleven’s Never-Ending Journey of Managing Data Protection & Mitigating Cybersecurity Threats

Wednesday, August 21st, 2024
Earlier this month Eight Eleven Group joined Brooksource, Medasource, and Calculated Hire in announcing that its enterprise sales and recruiting platform has earned certified status from HITRUST for information security. As the parent company for our three consulting and professional services companies, Eight Eleven Group provides operational support for over 32 markets. This support includes processing and storing valuable Personally Identifiable Information (PII) from our consultants and internal employees and maintaining the tech stack that makes business for all those individuals, and our clients, run smoothly. With a significant amount of data, organizations like Eight Eleven Group can be enticing targets for cyber threats and bad actors. This is why we pride ourselves on implementing and maintaining curated controls to protect against current and emerging cyber threats.
For those who are familiar with HITRUST, you understand why this recent achievement is something worth celebrating and highlights our dedication to keeping the Eight Eleven Family of Companies protected against security threats. However, not everyone is as familiar with HITRUST or the i1 Certification, so we sat down with Joe Essling, Eight Eleven Group’s Compliance Analyst for Information Security and leader of the organization’s certification process, to learn what this new certified status means for Eight Eleven Group and the individuals it serves.
ABOUT HITRUST & ITS CERTIFICATION OPTIONS
HITRUST is an information protection standards organization and certifying body for privacy, information security, and risk management. Organizations across various industries depend on HITRUST to audit, validate, and set the standards for their compliance goals and data security. HITRUST enables public and private sector organizations to safeguard sensitive data and manage emerging risks through its programs and certifications. It’s also worth noting that organizations and people CANNOT be HITRUST certified – HITRUST only assesses and certifies the data and systems an organization uses.
To accommodate for variation in the number of enterprise resources and associated risks of each organization, HITRUST has three certification options, each with a more intensive assessment and validation process. These options start with the entry e1 Certification that only focuses on essential cybersecurity controls, followed by the i1 Certification, and ending with the r2 Certification for organizations who need to demonstrate regulatory compliance for governing bodies like HIPPA or the National Institute of Standards and Technology (NIST). The HITRUST i1 Certification demonstrates that Eight Eleven Group’s cloud-centric approach to managing enterprise data is leveraging 182 curated controls to protect against current and emerging threats. Since the i1 Certification needs to be reassessed every year, HITRUST also helps organizations address cybersecurity challenges and remain cyber resilient over time.
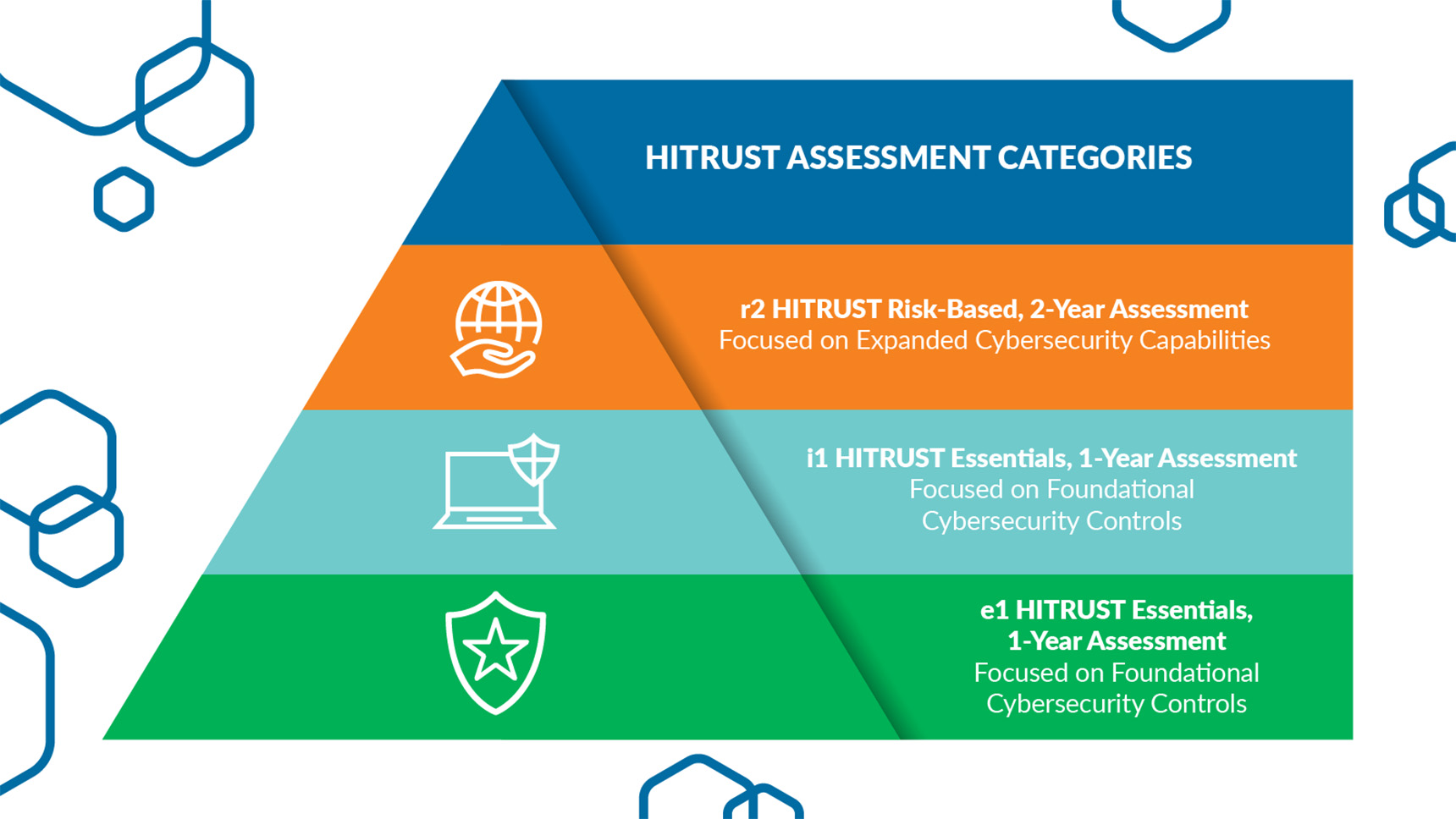
A breakdown of the different certification categories offered in HITRUST’s assessment portfolio.
The 5-Year Long Journey to Get Certified
The first step in HITRUST’s certification process for any organization is to partner with an authorized HITRUST External Assessor to complete a HITRUST readiness assessment. This self-assessment involved members of Eight Eleven Group’s IT department using the HITRUST CSF Framework to identify and document our enterprise resources, security measures, and privacy controls before collaborating with an authorized HITRUST External Assessor for the actual HITRUST Validated Assessment.

Eight Eleven’s Dedicated HITRUST Team (Left to Right): Nicholas Wallace, Jake Baldwin, Chad Coffey, Nick Tavassoli, Jon Theophilus, Mac Landwermeyer, & Joe Essling
Although the Eight Eleven Family of Companies has undergone a few phases of evolution and rebranding, it started as a staffing organization focused on the IT and Engineering industries. Because of this, the organization has always been an early adopter of the latest best practices and new technologies – even choosing to partner with some of the top IT and Cloud vendors. As Joe Essling explains, Eight Eleven’s vendor choices and status as a cloud-centric organization gave us a good starting point for the certification process.
“By leveraging industry-leading cloud and technology providers for our internal tech stack, we ‘inherit’ all the security controls that these vendors already have implemented into their product or service. Things like password complexity requirements, multi-factor authentication (MFA), and other security controls highlight that our vendors take the same deep consideration into their security environment as we do.”
- Joe Essling, Eight Eleven Group’s Compliance Analyst for Information Security
However, Joe also stressed that security controls are only part of the in-depth HITRUST CSF, which covers 19 different domains including topics like Incident Management and Education, Training, and Awareness. This thorough evaluation is one of the many reasons HITRUST is so respected in the compliance and cybersecurity community.
Once an organization has completed its readiness assessment, it will continue collaborating with its authorized HITRUST External Assessor for the actual HITRUST Validated Assessment. In our conversation with Joe, he emphasized that HITRUST’s use of third-party assessors is another way that HITRUST ensures the quality of each assessment. “Having external assessors means that the evaluation of our security controls was truly unbiased and thorough. Better yet, our external assessor brought a fresh set of eyes to identify the weak spots that we initially overlooked or didn’t consider, and then collaborated with us to address them” shared Joe. The identification of those blind spots comes in the form of a Corrective Action Plan (CAP) and each organization will be given a set amount of time to correct or close its security gaps before moving on with the certification process.
Only after an organization has completed this in-depth process and addressed the shortcomings outlined in its CAP will its HITRUST Validated Assessment be submitted. As an organization, HITRUST prides itself on the fact that each assessment submitted by a HITRUST Authorized External Assessor undergoes nearly 150 automated quality checks, as well as at least 5 levels of independent and objective quality review by Assurance Analysts within HITRUST’s Assurance team for validation. After HITRUST’s Assurance Team audits your assessment and denotes a passing score, the organization receives a letter of certification. If you’ve made it this far in the story, then it should come as no surprise that the Eight Eleven Family of Companies spent roughly 5 years preparing, assessing, and remediating its environment to achieve the i1 Certification.
Achieving HITRUST Certification Is Only the Beginning
After 5 years of hard work and thorough assessments by our IT department and external assessors, we have finally achieved our certification status. Although this accomplishment is worth celebrating, it does not mark the end of work with HITRUST to maintain our status. As Joe explains, “i1 Certification needs to be reassessed annually so each year HITRUST will ask us to demonstrate that we are following our program by randomly testing 60 of our 182 controls. If we fail on just 5 of these random controls, we could be subject to greater scrutiny during the recertification process where additional controls would be tested.” In addition to these reassessments, Joe also highlighted additional internal measures that have been put in place to ensure the latest best practices.

Joe Essling explains the dangers of phishing schemes and their use of emails to infiltrate organizations.
From continuous monitoring to updating controls, the Eight Eleven Family of Companies is taking a proactive approach to information security. Joe also leads ongoing training for our employees on security best practices and compliance requirements. “Yes, this certification provides external validation for our clients, consultants, and employees that we are protecting our internal data – but more importantly, it has created the framework for us to continue to build and maintain an emphasis on information security” highlights Joe.
As a parent company, Eight Eleven provides the vision and foundation for the growth of the Eight Eleven Family of Companies. Each company has been built with our customers' evolving needs in mind. Click here to read more insights and updates from the Eight Eleven Family of Companies!